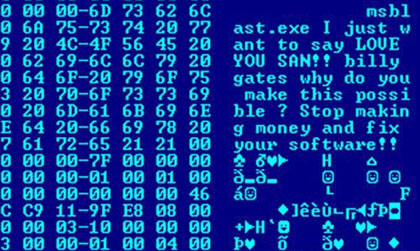
Hex dump of the Blaster worm, showing a message left for Microsoft CEO Bill Gates by the worm’s programmer
On November 10, 1983, U.S. student Fred Cohen at the University of Southern California‘s School of Engineering presented to a security seminar the results of his test, a program for a parasitic application that seized control of computer operations, one of the first computer viruses, created as an experiment in computer security.
John von Neumann – the “Father of Computer Virology”
But, the history of computer viruses dates back even further. The first academic work on the theory of self-replicating computer programs was performed in 1949 by John von Neumann who gave lectures at the University of Illinois about the “Theory and Organization of Complicated Automata“.[1] Von Neumann founded the field of cellular automata and did first experiments on self replicating automatons with pencil and paper. Later his work was published as the “Theory of self-reproducing automata“, where described how a computer program could be designed to reproduce itself. Von Neumann’s design for a self-reproducing computer program is considered the world’s first computer virus, and he is considered to be the theoretical father of computer virology.
Self-Reproducing Automata
Already in 1972, the Austrian computer scientist Veith Risak, directly building on von Neumann’s work on self-replication, published his article “Selbstreproduzierende Automaten mit minimaler Informationsübertragung” (Self-reproducing automata with minimal information exchange), in which he described a fully functional virus written in assembler language for a SIEMENS 4004/35 computer system. In 1980 Jürgen Kraus wrote his diplom thesis “Selbstreproduktion bei Programmen” (Self-reproduction of programs) at the University of Dortmund, in which he postulated that computer programs can behave in a way similar to biological viruses [2].
The Creeper
Also already in the ARPANET, the forerunner of today’s internet, there was a virus called Creeper. The Creeper virus was first detected on ARPANET in the early 1970s. It was an experimental self-replicating program written by Bob Thomas at BBN Technologies in 1971, which used the ARPANET to infect DEC PDP-10 computers running. Creeper gained access via the ARPANET and copied itself to the remote system where the message, “I’m the creeper, catch me if you can!” was displayed. The Reaper program was created to delete Creeper. In 1975, British author John Brunner published the novel The Shockwave Rider,[5] in which he foresaw the danger of Internet viruses. Also the idea of swarm intelligence is outlined in his story. The 1973 Michael Crichton sci-fi movie Westworld made an early mention of the concept of a computer virus, being a central plot theme that causes androids to run amok. In 1979, his colleague Thomas J. Ryan described in The Adolescence of P-1 how an artificial intelligence spreads virus-like across the national computer network.
The Birth of the “Computer Virus”
Then, in 1983, Fred Cohen, a student at the University of Southern California‘s School of Engineering, wrote a program for a parasitic application that seized control of computer operations in Leonard Adleman’s class – Adleman was one of the co-inventors of the RSA encryption. Cohen wrote a short program, as an experiment, that could “infect” computers, make copies of itself, and spread from one machine to another. It was hidden inside a larger, legitimate program, which was loaded into a computer on a floppy disk. In 1984, Fred Cohen wrote his paper “Computer Viruses – Theory and Experiments” [3]. It was the first paper to explicitly call a self-reproducing program a “virus”, a term introduced by Cohen’s mentor Leonard Adleman. In 1987, Fred Cohen published a demonstration that there is no algorithm that can perfectly detect all possible viruses. Fred Cohen’s theoretical compression virus was an example of a virus which was not malware, but was putatively benevolent. However, antivirus professionals do not accept the concept of benevolent viruses, as any desired function can be implemented without involving a virus. Any virus will by definition make unauthorized changes to a computer, which is undesirable even if no damage is done or intended.

Tequila Virus (1991, x86 MSDOS)
And the Virus became a Worm
Before computer networks became widespread, most viruses spread on removable media, particularly floppy disks. In the early days of the personal computer, many users regularly exchanged information and programs on floppies. Some viruses spread by infecting programs stored on these disks, while others installed themselves into the disk boot sector, ensuring that they would be run when the user booted the computer from the disk, usually inadvertently. Of course this should change with the advent of the internet. Then, the computer virus became a computer worm. A computer worm is a standalone malware self replicating computer program that is supposed to spread to other computers via a computer network. A computer worm relies on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer.
@mikkohypponen, DEFCON 19: The History and the Evolution of Computer Viruses [4]
References and Further Reading:
- [1] John von Neumann – Game Theory and the Digital Computer, SciHi Blog.
- [2] D. Bilar, E. Filiol (ed.) On self-reproducing computer programs, Master Thesis in Computer Science University of Dortmund, in Journal in Computer Virology February 2009, Volume 5, Issue 1, pp 9-87
- [3] Fred Cohen: Computer Viruses and Experiments, 1984
- [4] @mikkohypponen, DEFCON 19: The History and the Evolution of Computer Viruses, (2011), blackhattish @ youtube
- [5] John Brunner: The Shockwave Rider. Harper & Row, 1975
- [6] von Neumann, John (1966). “Theory of Self-Reproducing Automata“. Essays on Cellular Automata. University of Illinois Press: 66–87.
- [7] Computer Virus at Wikidata
- [8] “The Internet comes down with a virus”. The New York Times. August 6, 2014.
- [9] Timeline of Computer Security Exploits, via DBpedia and Wikidata






Pingback: Whewell’s Gazette: Year 2, Vol. #18 | Whewell's Ghost
Pingback: Computer Virus-from Annoyance to a serious threat
Pingback: Computer Virus-From Annoyance To A Serious Threat – Computer malware and viruses